Table of Contents
MacOS’s Airport
is a built-in wireless utility comes preinstalled in MacOS.
$ ll /usr/local/bin/airport
lrwxr-xr-x 1 root wheel 89 Jun 22 2016 /usr/local/bin/airport@ -> /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport
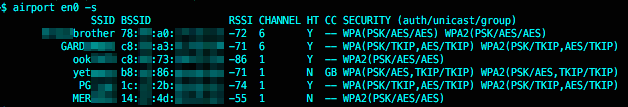
Perform a wireless broadcast scan to get the list of access points in the neighborhood:
Sniff 802.11 frames on channel 1, the output is in pcap format and can be opened with tcpdump/wireshark:
$ airport en0 sniff 1
Capturing 802.11 frames on en0.
^CSession saved to /tmp/airportSniffwUKb60.cap.
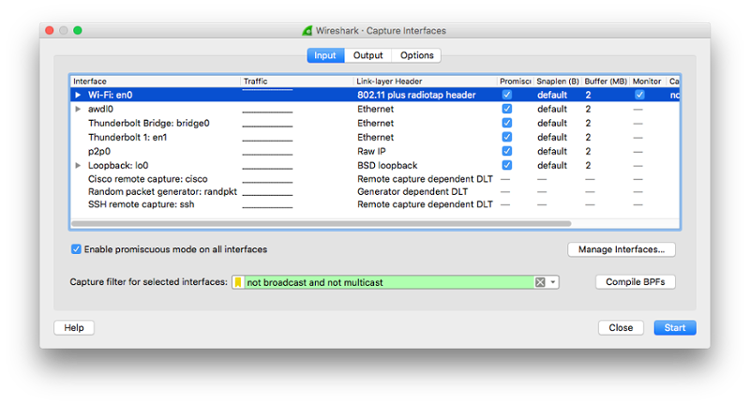
Wireshark
can also be used to capture wireless network traffic. To do that, open the wireshark’s capture option and select the Promiscuous and Monitor checkbox, optionally add capture filter 'not broadcast and not multicast' to filter out noises:
Since the wireless traffic is encrypted with WPA2, it won’t be useful unless decrypted. To enable decryption on-the-fly, navigate to Preferences → Protocols → IEEE 802.11, and select Enable decryption and add the decryption keys.
Depends on the type of encryption used, the following lists the WEP, WPA-PWD and WPA-PSK format:
wep:a1:b2:c3:d4:e5wpa-pwd:myPassword:mySSIDwpa-psk:0102030405060708091011...6061626364
To generate the WPA-PSK of your wireless credentials, use the WPA-PSK Generator[1] provided by Wireshark.
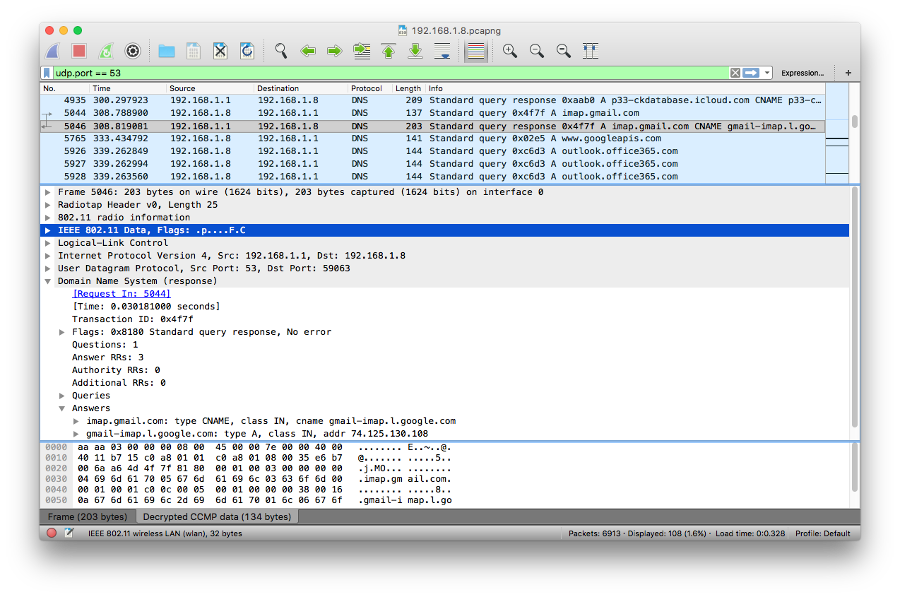
In order to capture the handshake for a machine, force the machine to (re-)join the network while the capture is in progress. Repeat this for all machines whose traffic you want to see. Figure below shows the captured/decrypted DNS traffic.
References: