Table of Contents
Introduction
The process is mostly the same in network packets data-carving, which comprises of:
- Gain access and collect the raw bytes
- Strip the protocol information
- Extract and write the data to file
The differences of these tools are their capabilities i.e., the supported protocols and file formats.
Wireshark
HTTP objects and files
To extracts the HTTP objects and files with Wireshark,
-
Navigate to ‘File’ → ‘Export Objects’ and select the type, currently it supports four protocols:
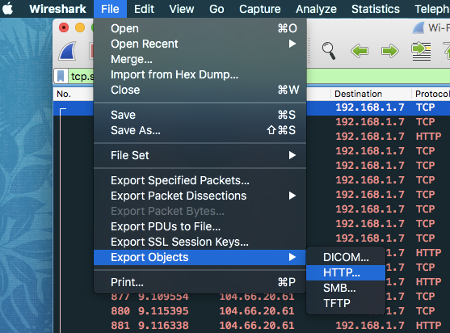
-
Then select the target filename followed by ‘Save’ or simply ‘Save All’:
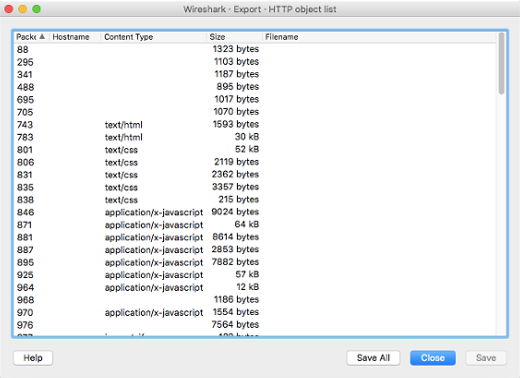
-
Once extracted, the list of exported objects and the respective file types can be seen:
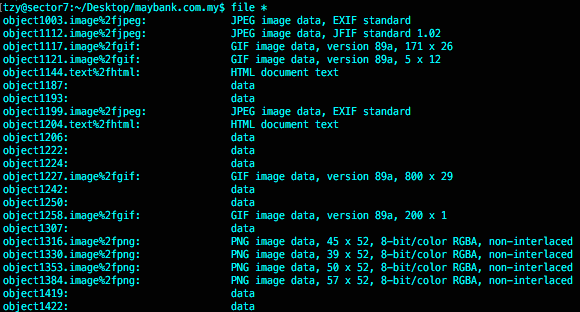
-
Alternatively, the ‘Follow’ → ‘TCP Stream’ can also be used to extract raw files from the stream:
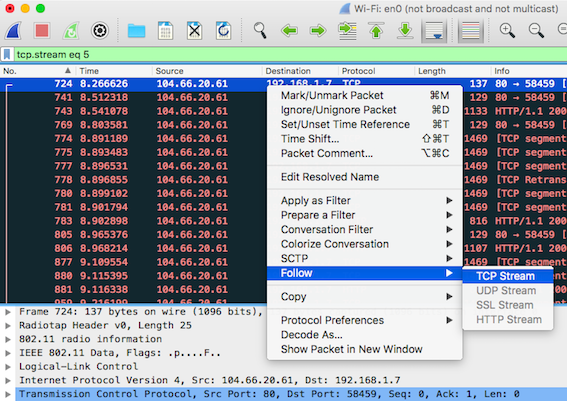
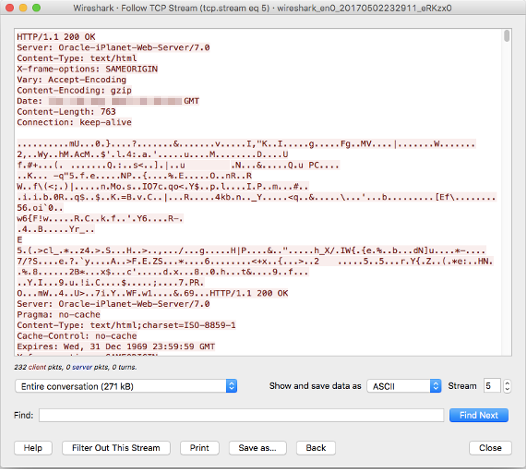
Binary files
In real world scenario, malware often spread through http protocol, thus we could search the common strings used by malware such as GetProcAddress, ExitProcess and etc. (statistically reported in paper by Gong et al. [1]).
-
To get to that for extraction purposes, use the display filter '
http contains "GetProcAddress"' :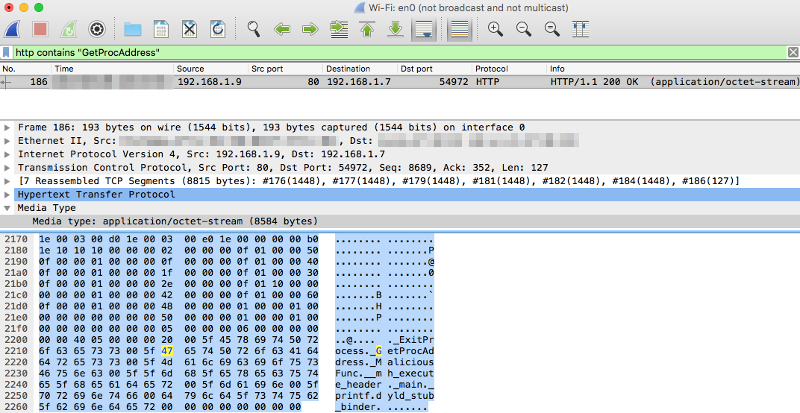
-
There are multiple ways to export the packets (binary file):
-
‘Export Objects’ → ‘HTTP’, and select the file from the list:
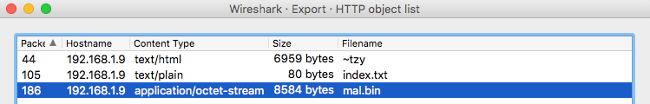
-
Or, right-click and ‘Export Packet Bytes’:
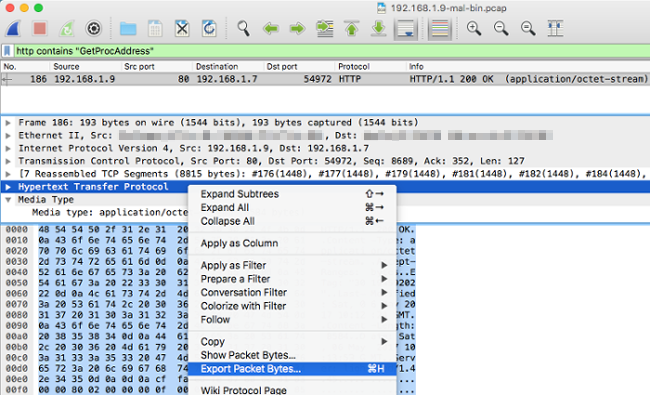
-
-
Once the binary is obtained, we could use hex editor to view the binary file, and locate the matching strings:
$ xxd mal.bin |less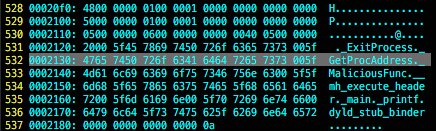
-
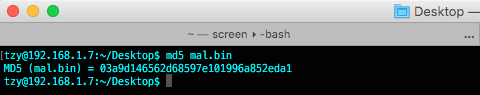
And start attribution and digital signature with fingerprinting the binary with MD5 checksum, etc. :
Tcpflow & Foremost
Assuming the pcap file 192.168.1.0.pcap contains the packets captured from the 192.168.1.0/24 network, we could use tcpflow to extract the data streams into individual files by ip-addresses:
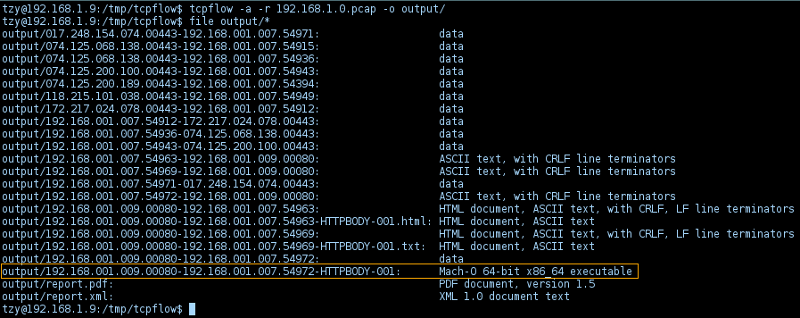
-
Tcpflowonly handles the direction of the data streams, and if the target binary files were not split into individual files bytcpflow, we could useforemostutility to complement the processes:Note: add the following line to
/etc/foremost.confto add Mach-O binary file format’s signature.bin n 4096000 \xCF\xFA\xED\xFE\x07\x00where,
[filetype] [case-sensitivity] [upper-limit-for-size] [signature header] [footer] -
Concatenate the data files generated by
tcpflowinto a single file: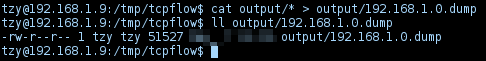
-
Parse the file with
foremost, followed by validation with md5sum which yielded identical result to previous digital signature fingerprint ofmal.binfile extracted withwiresharkin above section from host192.168.1.7: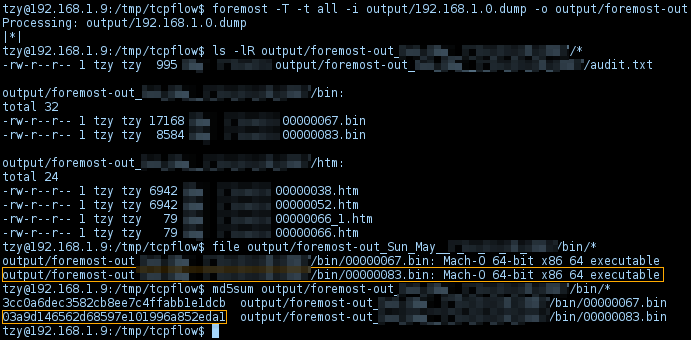
Note: tcpflow only support TCP packets, it does not handle UDP packets. To separate the packets not processed by tcpflow, use the -w option:
-w filename.pcap
Write packets that were not processed to filename.pcap. Typically this will be UDP packets.
References:
- Gong, M., Girkar, U., & Xie, B. Classifying Windows Malware with Static Analysis.
- https://www.sans.org/reading-room/whitepapers/forensics/extracting-files-network-packet-captures-36562