Table of Contents
Nettop
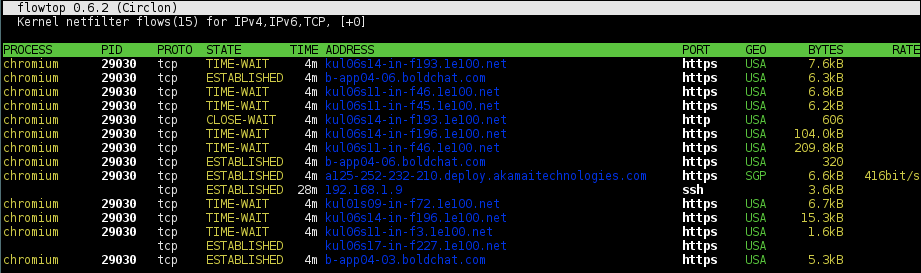
Assuming an unknown/suspicious output (i.e., no chat client is being used, but random chat domain appeared: vmp.boldchat.com) is spotted from a DNS monitoring such as in previous post titled - Sniff DNS queries:
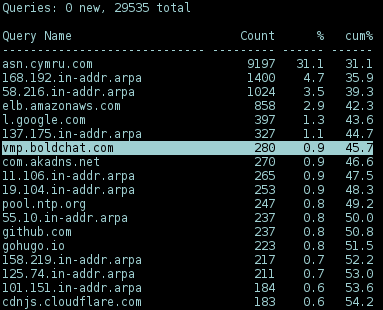
Under macOS, the nettop util provides list of sockets and routes in details that help to trace down the process that established the connection to the unknown domain:
use keys to toggle:
d, delta output
c, collapse all
e, expand all
j, bring up the column selection menu
h, help
$ nettop
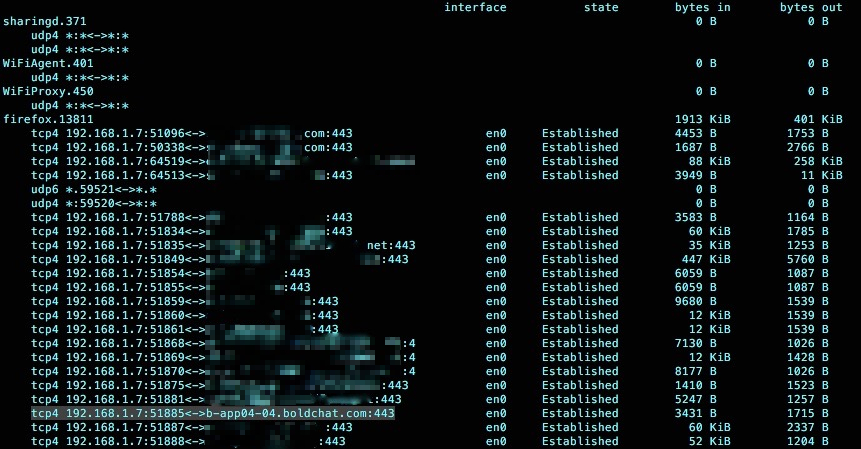
Google Transparency Report: Safe Browsing Tool
Since the process is from Firefox on port https (443), the Google Transparency Report Safe Browsing tool can be used to check if the site is malicious and unsafe.
Netstat
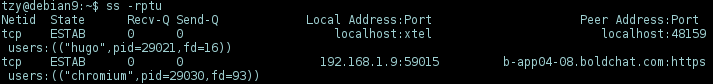
On linux, ss or netstat can be used:
-l, --listening display listening sockets
-n, --numeric don't resolve service names
-p, --program show the pid/name of the program
-r, --resolve resolve numeric address/ports
-t, --tcp display only TCP sockets
-u, --udp display only UDP sockets
$ ss -rptu
Similarly, netstat would work too:
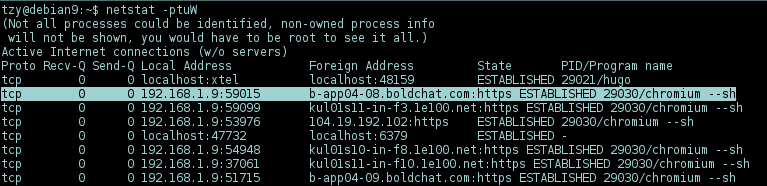
$ sudo netstat -ptuW <- (to see non-owned process info)
Flowtop
The flowtop from the netsniff-ng package also works: